A security operating model enables an organization to focus on identifying risks, recommending risk responses, facilitating tradeoff decisions related to these risks, and providing a line of sight to the execution of these responses. The core of this model is a collaborative continuous improvement process designed to sustain the controls that secure the enterprise. You can learn more about the advantages of a security operating model in “The Security Operating Model: A Strategic Approach for Building a More Secure Organization.”
This article will dive deeper into one of the six areas of focus for developing and maintaining a security operating model: the risk-based business plan. A risk-based plan will help answer questions such as:
- How can you ensure your resources are allocated appropriately across the organization?
- When the environment changes, how can you easily identify gaps, prioritize opportunities, and shift your resources accordingly?
- Are your resources allocated to areas of greatest risk?
- Are you proactively managing security risks or just reacting to them?
The business plan is a powerful tool to ensure alignment across the operating model. A business plan is composed of focus areas that support the organization’s overall vision. Each focus area is further broken down into time-based objectives and measurable supporting tactical initiatives. This tiered model enables the organization to deliberately align every budgeted dollar to an identified risk, while transparently measuring the outcomes versus objects.
The objective of the business plan is to appropriately allocate security resources based on the risks to the organization. Some key points to consider while constructing a risk-based business plan include:
- Assess your high-priority risks and address them via your industry-based risk treatment plan. This is a critical point and should not be ignored. This allows an organization to understand the residual security risk the organization is accepting based on the implementation of a security controls framework, core function performance, and control compliance metrics. The comprehensive nature of this information provides the backbone for the organization’s security and illustrates the strengths and potential weaknesses of the holistic enterprise security posture.
- Evaluate your current security maturity and simultaneously use the risk-to-maturity curve (see Figure 1) to identify the most impactful security investments to build out your security program. Collaboratively defining current and target state capability maturity enables an organization to deliberately allocate resources to close capability gaps and regularly measure their progress.
The risk-to-maturity curve provides a structured, methodical, and industry-supported approach to informing and communicating business plan investment decisions. It positions these decisions based on how well they reduce risk and increase security maturity.
Figure 1: Risk-to-Maturity Curve
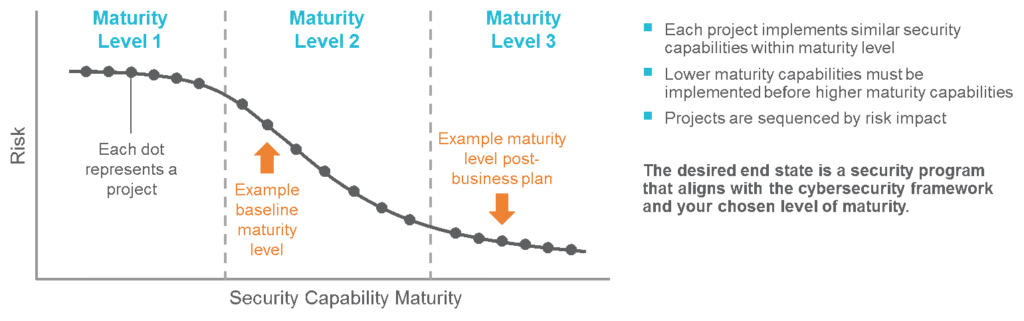
This approach allows you to address urgent needs while continuously improving your security posture. Use the risk-to-maturity curve to communicate current capabilities, the business plan to demonstrate which risks are being addressed, and both to discuss where you expect to be on the curve over the next planning cycle.
This entire process is done holistically, involving multiple internal and external stakeholders. Without this crucial alignment, plans are often developed in silos and neither the external stakeholders nor executive leadership are included in the process until the very end. This can lead to uninformed decisions, lack of organizational support, and misalignment across the entire model. Collaboratively developing the plan with stakeholders is as important as the actual contents of the plan.
Monitoring the performance of your business plan and operating model hinges on security metrics and reporting, oversight, and management controls. To learn more about these critical features, keep an eye out for the next installment of our security series focused on metrics and management controls.
Additional Contributing Author: Hayden Overly